In the modern digital age, where the world is connected by a web of intricate networks, the term “cyber attack” has become synonymous with danger and disruption. As technology advances, so do the tactics and techniques employed by cybercriminals, making it imperative for individuals, organizations, and governments to comprehend the intricacies of cyber attacks. In this blog, we delve into the world of cyber attacks – shedding light on their various forms, exploring their motivations, and outlining strategies to defend against these digital onslaughts.
The Spectrum of Cyber Attacks
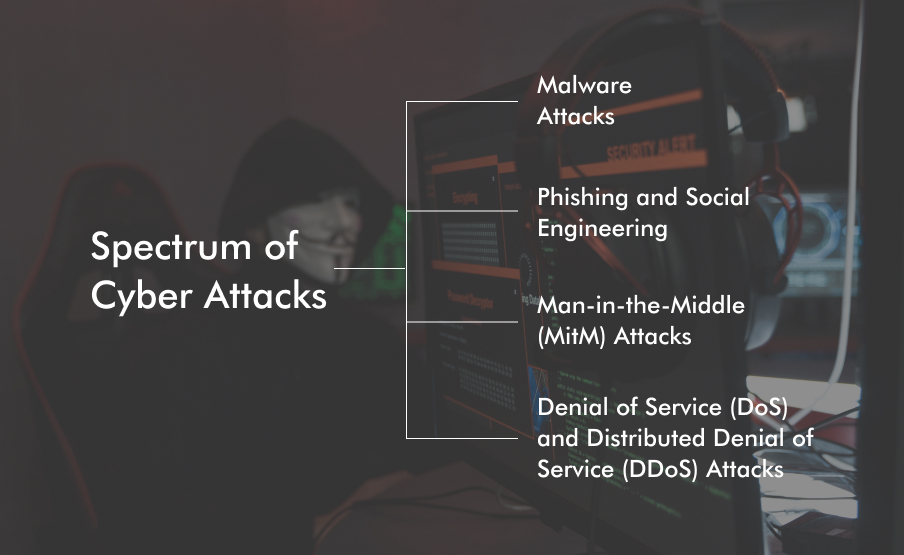
Cyber attacks encompass a diverse range of tactics designed to exploit vulnerabilities and compromise digital systems. Some of the most common types include:
1. Malware Attacks:
Malicious software, or malware, is a common weapon in a cyber criminal’s arsenal. This includes viruses, worms, Trojans, and ransomware, which are designed to infiltrate systems, steal sensitive data, or hold it hostage for ransom.
2. Phishing and Social Engineering:
These attacks prey on human psychology, using deceptive tactics to manipulate individuals into revealing confidential information or performing actions that compromise security.
3. Denial of Service (DoS) and Distributed Denial of Service (DDoS) Attacks:
These attacks overwhelm a target’s systems with an excessive volume of traffic, rendering them unavailable and disrupting normal operations.
4. Man-in-the-Middle (MitM) Attacks:
Cybercriminals intercept and alter communication between parties, enabling them to eavesdrop on sensitive information.
5. Zero-Day Exploits:
These attacks take advantage of previously unknown vulnerabilities in software before developers have a chance to patch them.
The Underlying Motivations: What Drives Cyber Attacks?
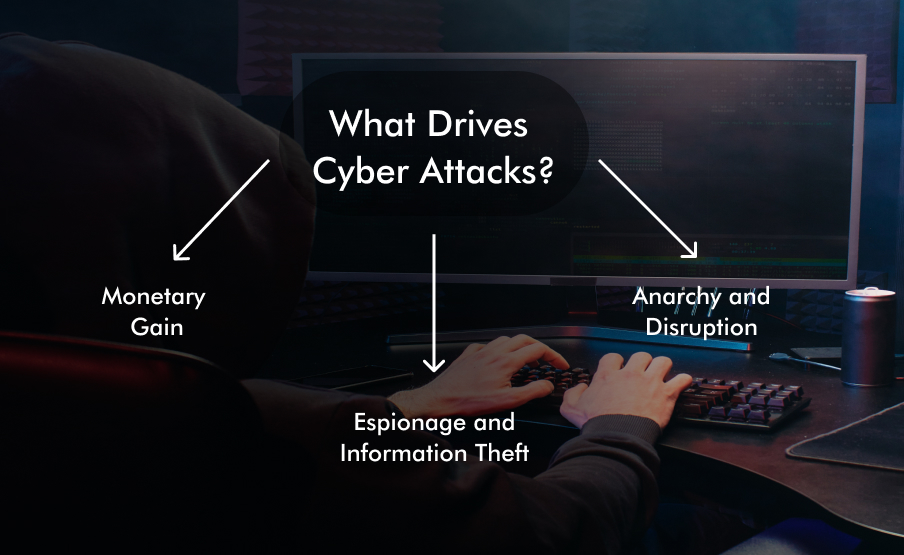
Understanding the motives behind cyber attacks uncovers a mosaic of incentives:
1. Monetary Gain
Financially motivated attacks seek to pilfer sensitive data, credit card information, or cryptocurrency for illicit profit.
2. Espionage and Information Theft:
State-sponsored assaults and corporate espionage aim to pilfer valuable data, trade secrets, and intellectual property.
3. Anarchy and Disruption:
Certain attackers revel in chaos, targeting systems to sow discord, disrupt services, or amplify their notoriety.
Defending Against Cyber Attacks

Proactive defense is essential in the face of ever-evolving cyber threats:
1. Cyber Hygiene:
Regularly update software, use strong, unique passwords, and be cautious of suspicious emails and links.
2. Firewalls and Intrusion Detection Systems
Employ these technologies to monitor and block unauthorized access.
3. Employee Training:
Educate staff about phishing, social engineering, and other attack vectors to prevent inadvertent breaches.
4. Data Encryption:
Protect sensitive data by encrypting it both in transit and at rest.
5. Patch Management:
Keep software and systems up to date to minimize vulnerabilities.
6. Incident Response Plans:
Develop a comprehensive plan to swiftly respond to and mitigate the effects of a cyber attack.
CodersBucket: A Beacon of Digital Resilience

In the face of these evolving threats, CodersBucket emerges as your steadfast guardian, offering tailored solutions to secure your digital presence:
1. Holistic Cybersecurity Strategies:
CodersBucket’s expert team employs a multi-layered approach, integrating firewalls, intrusion detection, and encryption to create a robust digital bulwark.
2. Swift Incident Response:
CodersBucket equips you with a comprehensive incident response plan, enabling quick containment and damage mitigation in the event of an attack.
3. Technological Prowess:
Harness the power of advanced technologies like AI-driven threat detection and secure coding practices, empowering your defense against emerging risks.
4. Cultivating Cyber Literacy:
CodersBucket provides extensive employee training, fostering a culture of cyber awareness and minimizing the risk of human error-based breaches.
Elevate Your Digital Resilience with CodersBucket
CodersBucket isn’t just a software company – it’s your strategic partner in the realm of digital security. With CodersBucket, you gain an ally that combines expertise, innovation, and unwavering commitment to protect your digital assets and ensure uninterrupted success.
Forge a path of digital resilience alongside CodersBucket. Explore our offerings and fortify your defense at www.codersbucket.com.
Together, we’ll unveil the shadows, confront the threats, and empower you to thrive in the digital age. Your security is our mission, and your triumph is our journey!